Category: AI News


Smart Cities Powered by IoT

IoT Security and Privacy Challenges

NFTs and the Future of Digital Assets
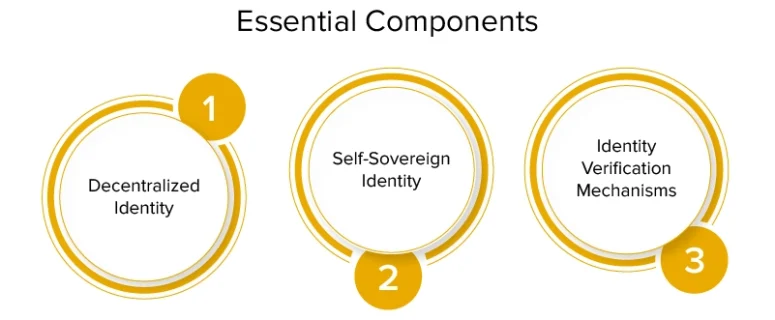
Blockchain for Digital Identity

Ethics and Challenges of AIGC

AI-Generated Content in Digital Marketing
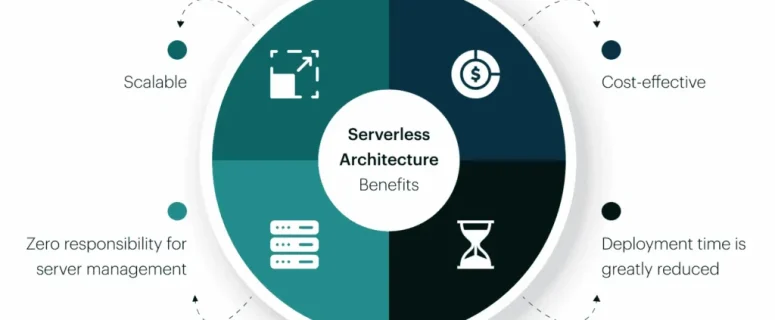
Serverless for Scalable Applications
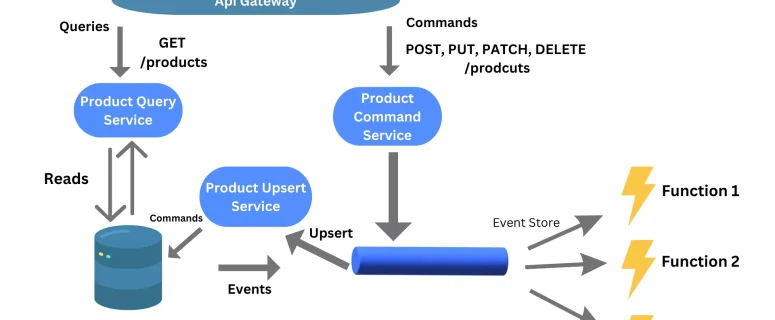
Event-Driven Design Patterns in Serverless

Quantum Computing in Cybersecurity
Ad Blocker Detected
Our website is made possible by displaying online advertisements to our visitors. Please consider supporting us by disabling your ad blocker.
